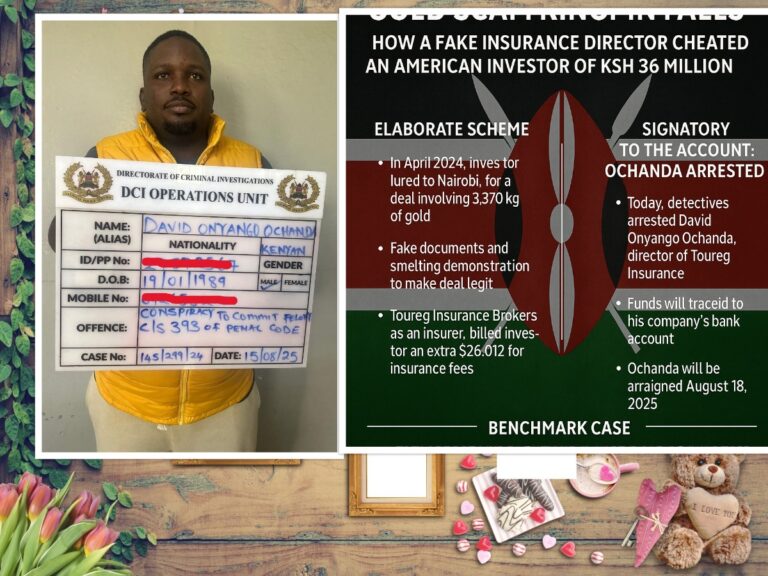
The Crucial Role of Cyber Insurance for Businesses
Introduction
In an era dominated by digital advancements, businesses are increasingly reliant on technology to streamline operations and connect with their audience. However, this dependency on digital infrastructure comes with its own set of risks, primarily in the form of cyber threats. As cyberattacks become more sophisticated and prevalent, businesses are recognizing the need for robust cybersecurity measures. One essential component of a comprehensive cybersecurity strategy is cyber insurance.
Understanding Cyber Insurance
Cyber insurance, also known as cyber liability insurance or cyber risk insurance, is a specialized insurance product designed to protect businesses from the financial repercussions of a cyberattack. Unlike traditional insurance policies that cover physical damages, cyber insurance focuses on the intangible yet critical assets that businesses possess—data and digital infrastructure.
Key Elements of Cyber Insurance
- Data Breach Coverage: One of the primary features of cyber insurance is coverage for data breaches. In the event of unauthorized access or theft of sensitive information, the policy helps cover the costs associated with notifying affected parties, providing credit monitoring services, and handling public relations to mitigate reputational damage.
- Business Interruption Coverage: Cyberattacks can disrupt business operations, leading to financial losses. Cyber insurance often includes coverage for business interruption, compensating the business for lost income during downtime caused by a cyber incident.
- Ransomware Protection: With the rise of ransomware attacks, businesses are increasingly vulnerable to extortion demands. Cyber insurance can provide coverage for ransom payments and the associated expenses of dealing with a ransomware incident.
- Legal Expenses: Cyber incidents may lead to legal actions from affected parties. Cyber insurance policies typically cover legal expenses, including hiring legal professionals and covering settlement costs.
- Forensic Investigation Costs: Determining the cause and extent of a cyberattack requires specialized forensic investigation. Cyber insurance helps cover the expenses associated with investigating the incident, identifying vulnerabilities, and implementing preventive measures.
The Growing Need for Cyber Insurance
As cyber threats evolve, businesses of all sizes and industries face an elevated risk of falling victim to a cyberattack. The consequences of such incidents can be severe, ranging from financial losses and reputational damage to regulatory penalties. Here are some factors contributing to the growing need for cyber insurance:
- Increased Frequency and Sophistication of Attacks: Cybercriminals continually refine their tactics, making it challenging for businesses to stay ahead. The growing frequency and sophistication of cyberattacks highlight the importance of having a financial safety net in the form of cyber insurance.
- Regulatory Scrutiny and Compliance Requirements: Governments and regulatory bodies are imposing stricter data protection regulations. Non-compliance can result in hefty fines. Cyber insurance helps businesses meet regulatory requirements and manage the financial consequences of potential penalties.
- Global Interconnectedness: In an interconnected world, a cyber incident can have far-reaching consequences. Businesses with international operations or those connected to global supply chains recognize the need for comprehensive cyber insurance coverage to address the potential ripple effects of a cyberattack.
- Dependency on Digital Assets: As businesses increasingly digitize their operations, the value of digital assets such as customer data, intellectual property, and proprietary information grows. Cyber insurance protects these assets, acknowledging their importance in the modern business landscape.
- Third-Party Risks: Businesses often collaborate with third-party vendors and partners, creating additional avenues for cyber threats. Cyber insurance not only covers direct losses but also provides protection against liabilities arising from third-party breaches.
Implementing Cyber Insurance in Business Strategy
- Risk Assessment: Before purchasing cyber insurance, businesses should conduct a thorough risk assessment. Understanding the specific cyber risks they face allows organizations to tailor their insurance coverage to meet their unique needs.
- Policy Customization: Cyber insurance policies are not one-size-fits-all. Businesses should work closely with insurance providers to customize policies based on their risk profile, industry regulations, and the nature of their digital assets.
- Employee Training and Cyber Hygiene: Insurance alone is not a silver bullet. Businesses should prioritize employee training to enhance cybersecurity awareness and promote good cyber hygiene practices. Proactive measures can reduce the likelihood of a successful cyberattack.
- Incident Response Planning: Having a robust incident response plan is crucial. Cyber insurance providers often offer guidance in developing effective response strategies, ensuring that businesses can minimize damage and recover quickly in the event of an incident.
Conclusion
In the digital age, cyber insurance has become an integral component of a comprehensive risk management strategy for businesses. As cyber threats continue to evolve, the financial and reputational consequences of a cyberattack can be devastating. Cyber insurance not only provides a financial safety net but also encourages businesses to adopt proactive cybersecurity measures, making it a valuable investment in today’s interconnected and digitized business landscape. By understanding the risks, customizing policies, and integrating cyber insurance into their overall strategy, businesses can navigate the digital frontier with confidence and resilience.